…or: The need of protecting users from themselves.
How do you obtain software for your Linux-Distribution? Right, you fire up the package management tool and install packages provided by your distributor. You can always be sure that these packages work well with your system (at least they should do it :P) and do not contain malware.
But what do you do if you want to install the shiny-new version X of application Y, which is not yet in the archives? Or what do you do if you, for example, want to install a proprietary Linux-game? Ubuntu users search Launchpad for a so-called “PPA” (Personal Package Archive) which is a public software source which is added to the distribution software sources.
This has some great advantages:
- You can install PPAs easily
- You always get fresh updates using the generic Update-Manager
- It is nicely integrated with other parts of the system
However, there a also some disadvantages, which make PPAs in my opinion unusable for software distribution (they have never meant to be public package archives instead of personal package archives anyway:
- Security: If a package contains malware, it will have root-access to the full system. A native distribution package can do nearly anything with it.
- Quality: Packaging is (what some people don’t know) not only taking the upstream tarball and putting it into a DEB package. There are a lot of quality standards to comply with. These standards (e.g. the Debian packaging policy) are there for a specific reason: To keep the distribution stable and to avoid packaging errors. With PPAs you can never be sure if all guidelines have been followed, so you will probably install a “bad” package which causes conflicts with other software.
- Upgrades: If you install new versions of a package, old packages provided by your distributor get replaced. And even through adding new packages, you might break your distribution’s upgrade-path, so an upgrade to a newer distribution-release will fail.
- Ubuntu-Centric: PPAs are Ubuntu-only. There’s no Fedora support and no Debian support too. A cross-distro solution would be better.
So I developed Listaller, a cross-distro tool to install 3rd-party software. But installing 3rd-party software is always risky, as you can install e.g. a new Mediaplayer, but the new Mediaplayer could also be some new malware which damages your system or steals your private data. It could also be possible that you install a crappy package which damages something in your system.
So, how do we prevent this? How can we allow 3rd-party installations which are standard-compliant and safe?
Apple showed a very simple way: For their iPhone, they check every application which wants to be included into the Apple AppStore manually, so users won’t install malware. Canonical is planning something similar, but more open.
This approach can’t be a solution for the problem above, at least not for the Linux/FLOSS world. As soon as you can install & execute any software you like, there is the risk to install crap. Look at some Windows-Desktops for example, then you know what I mean 😛 So, users need to be aware of what they’re doing if they install an application, they need to think.
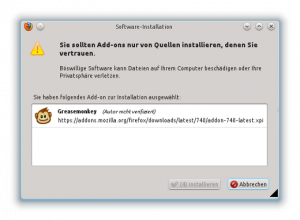
Okay, how can we make people think? Uhm… Mozilla decided to add a delay of 6 seconds before installing software/a Firefox addon:
The warning triangle reminds user not to install software they don’t trust. The delay should make users read the text above the button.
Theoretically this works fine, but in fact users will only find it nasty to wait until the delay is over, do other things while waiting and won’t read the text.
Also, how should users know if they trust this AddOn? The website said they can trust this download, so …
Also, I don’t think many users think much before they install software – they want to “have it” right now, they want to use it and not worry about security aspects.
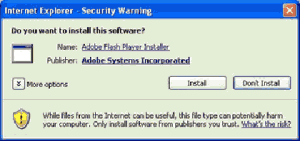
Windows is a little bit different in this case: They check signatures of an executable downloaded from the Internet and display a dialog, printing some information about this software as well as the warning “This file type can harm your computer”. This is also not interesting for many people – they already know that executables can harm their systems.
So, what about displaying some technical information, so users know what’s going on?
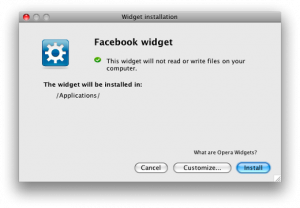
“Widget will be installed into /Applications” – nice! But users won’t know how to interpret technical information, so this is also not the way to go.
So, how can we prevent users from installing malicious software and damaging their system or sending their private data over the Internet to some unauthorized 3rd-party? The answer is simple: We can’t do this and we will never be able to exclude the possibility of installing malware (at least if we don’t want an Apple-like solution). But we can minimize the chance of installing malware. The examples above show, that displaying warning dialogs before installations to make users think about their next clicks does only work in a few cases.
So I propose we don’t show this kind of dialog before installation. Instead tools like Listaller will simply reject untrusted packages, e.g. packages which were not GPG-signed. Users need to change Listaller’s configuration manually to install this software then. This is an effort users will only take if they are sure they want this software.
Also, displaying useful dialogs about GPG signatures will help people a lot if they want to decide if they trust a package.
Take this dialog from the ZeroInstall software distribution system as an example:
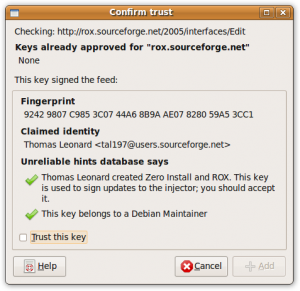
It shows nicely why users should trust software signed with this key, so users can decide if they really want to install it. (For example “Key belongs to a Debian maintainer” usually is a sign that someone with extended Linux knowledge created this package)
There are also some other ways to limit the danger of damaging the system via a 3rd-party software installation. To minimize policy-incompliant installations, the installer-program should decide how to install an application – not the person who created the package. So distributions just need to change the installer-code to make 3rd-party application installs compliant with their specs.
By disallowing “dangerous” features like running custom scripts during installations and by running all 3rd-party apps in a sandbox by default the danger of malware is also minimized.
Compared to a PPA, where packages can do nearly everything, the Listaller solution or a Listaller-like solution would be the best approach in Linux software-distribution for most applications. If a tool really needs full control over it’s setup (which can only be a system-internal app/daemon or a library, IMO) it could use a native PPA.
As much as I dislike the GNOME principle of patronizing users in how they should do their work (less settings etc.) in the case of 3rd-party software installations it seems to be the only way of making them a little bit more secure.
This here is just a loose collection of thoughts at time, but some of this will probably be implemented in Listaller during the next months.
Hi,
My name is Adela and I’ve found your company via google. I’m editor of Pentest Magazine and I’m preparing the special issue on Nessus and Scanning topics. I would like to invite you to write an article/articles for our magazine I think that you have a lot to say and you can share your knowledge with our readers and help us create the best issue on that. I can help you promote your company among our readers that we have almost 100.000, mainly security experts.
I will be waiting for your thoughts on this.
Sincerely,
Adela Kuźniarska
PenTest Magazine